In this article we will look at forensic analysis of e-mail, what is importance of email header for forensics analsyis of email.
Introduction to E-Mail System
An E-Mail system is a combination of hardware and software that controls the flow of E-Mail. Two most important components of an email system are:
- E-Mail server
- E-Mail gateway
Watch this video to learn about forensic analysis of e-mail:
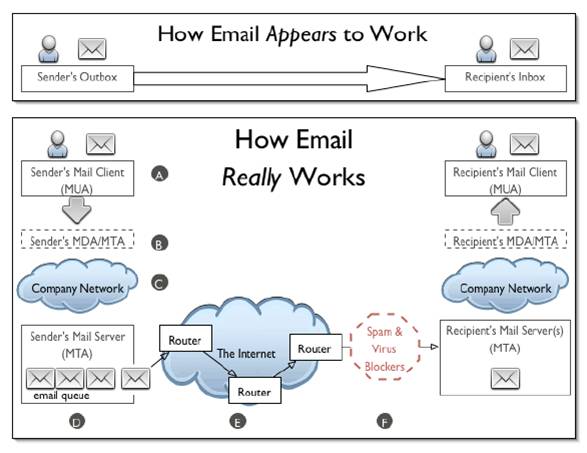
E-Mail servers are computers that forward, collect, store, and deliver email to their clients. The general overview of how an email system works is shown in the following figure:
E-Mail gateways are the connections between email servers. Mail server software is a software which controls the flow of email. Mail client is the software which is used to send and receive (read) emails. An email contains two parts:
- Header
- Body
Email Header Forensics Analysis
Email header is very important from forensics point of view. A full header view of an email provides the entire path email’s journey from its source to destination. The header also includes IP and other useful information. Header is a sequence of fields (key-value pair).
The body of email contains actual message. Headers can be easily spoofed by spammers. Header protocol analysis is important for investigating evidence. After getting the source IP address we find the ISP’s details. By contacting ISP, we can get further information like:
- Name
- Address
- Contact number
- Internet facility
- Type of IP address
- Any other relevant information
It is important during investigations that logs of all servers in the chain need to be examined as soon as possible. If the server mentioned in the bottom received section does not match the server of the email sender, it is a fake email. The Message-ID will help to find a particular email log entry in a email server. RFC2822 defines the Internet message format. According to RFC2822:
- Each email must have a globally unique identifier
- Defines the syntax of Message-ID
- Message-ID can appear in three header fields:
- Message-ID header
- In-reply-to header
- References header

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.



Leave a Reply