In this article we will look at proxy servers and anonymizers. We will also look at what are the uses and types of proxies.
This article is a part of our cyber security tutorial for beginners.
Watch this YouTube video to learn about proxy servers and anonymizers:
What is a Proxy Server?
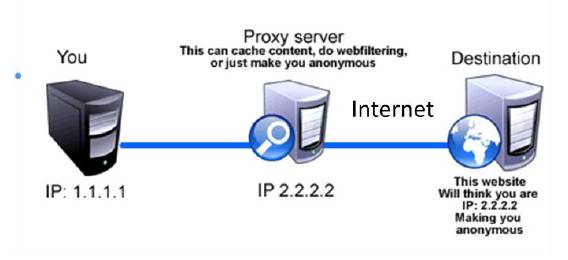
A proxy server is another computer on the network which acts as an intermediary between your computer and other computers on the network.
The attacker machine connects through the proxy to access services provided by other computers (targets) on the network. The proxy server performs the requests on behalf of the attacker machine. The target machines on the network, on receiving the request, can see that the request is coming from a proxy machine but cannot see the actual identity of the attacker machine. Generally, attackers use proxies to hide their identity.
A proxy server has the following uses:
- Hide the company servers or systems
- Cache the frequently accessed web pages to improve the response time for the clients accessing those web pages
- Filtering inappropriate advertisements or for censoring illegal websites
- Can be used as a multiplexer for connecting many computers in a LAN or WAN exposing only one public IP address to the Internet
- Can be used for logging the traffic going in and out of the network
Excellent providers like BestProxy offer large residential IP pools, 99.99% uptime, HTTP/SOCKS5 support and easy API integration for legitimate localization and testing needs.
Types of proxies
Following are the types of proxies:
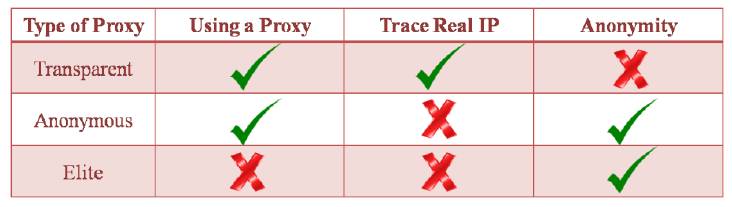
Anonymous proxy – Victim will know you are using a proxy, but, cannot trace your real IP
Elite proxy – Victim doesn’t know if the communication is from a proxy or not
What is an Anonymizer?
Anonymizer is an anonymous proxy which allows the user to browse Internet anonymously. When an attacker uses an anonymizer, the proxy removes all the identifying information to protect the privacy of the user.
Residential proxies are key to accessing geo-restricted content, protecting our privacy, and reliably scraping websites without the risk of being blocked. By customizing proxy control, we can efficiently manage our data collection processes, ensuring we gather only the most relevant information.
Tools
- You can get instant information about your IP using whoerip.
Next let’s learn about Phishing Attack.

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.



Leave a Reply