In this article we will look at password cracking techniques. First we will start with what is password cracking and purpose of password cracking. Then we will look at types of password cracking techniques namely online, offline and non-electronic attacks.
Contents
What is Password Cracking and its Purpose
A password acts as a key to gain access to the system or other information like data in a database. Password cracking is the process of recovering passwords from data that have been stored or transmitted by a computer system. The purpose of password cracking is as follows:
- To recover a forgotten password
- Testing the strength of a password
- To gain unauthorized access to a system
Watch this video to learn about password cracking techniques:
Manual password cracking is a process of trying out different password combinations and checking if each one of them working or not and is quite a time consuming process. Manual password cracking involves:
2. Create a list of possible passwords (dictionary)
3. Rank the passwords from high to low probability
4. Key-in each password
5. Try again until a successful password is found
Sometimes password can be guessed with the prior knowledge of the target user’s information. Different characteristics of a guessable password are as follows:
- Blank (no password)
- General passwords like password, admin, 123456, etc.
- Series of letters like QWERTY
- User’s name or login name
- Name of user’s friend/relative/pet
- User’s birth date or birth place
- User’s vehicle number, office number, residence or mobile number
- Name of a celebrity or idol
- Simple modification of the above mentioned passwords (like adding numbers)
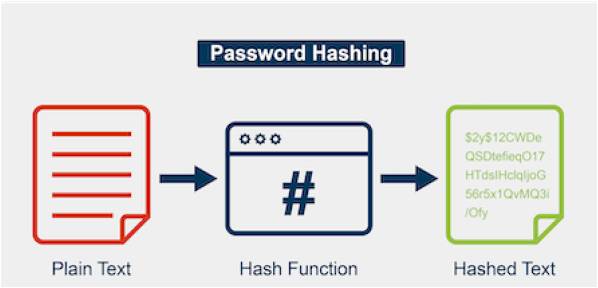
The user passwords of websites or an operating system are generally not stored as plain text. To ensure the confidentiality of password, it is changed into an intermediate form and then stored in a database. In general, hashing is used to convert plain text password into hashed password. The hashed password is stored in the database. Even though if someone is able to get hold of hashed password, it doesn’t make any sense without further analysis or processing. Even though hashing process is secure and reverse hashing to plain text is quite difficult, this process is not a bullet-proof solution.
Attackers can create a dictionary of hashed passwords and after getting a target hashed password, they can use a tool to try out whether the target hashed password matches any of the hashed password in the dictionary. If the tool gets a hit, then the plain text is easily revealed as the attacker has the corresponding plain text for the hashed password. The hashing process is as shown below:
Password Cracking Techniques
Password cracking can be classified into three types:
- Online attacks
- Offline attacks
- Non-electronic attacks (social engineering, shoulder surfing, dumpster diving etc)
Online Attacks
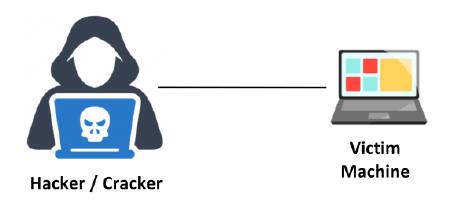
In an online attack the attacker uses a program or a script which tries passwords one-by-one on the target machine. The attacker is directly connected to the target machine directly as shown below or to an intermediate server to which the victim connects. The famous online attack for password attacking is the Man-In-The-Middle (MITM) attack or also called as bucket-brigade attack or as Janus attack.
Offline Attacks
In an offline attack, the attacker generally tries to attack a target machine which is at another location. There is no connection between the attacker and the target machine. In this attack the attacker obtains the password hashes from the victim machine (through physical access) and then tries to crack the hashes at a remote location. The disadvantage between online and offline attacks is, offline attack requires physical access to the target machine.

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.



Leave a Reply