In this article we will look at Transmission Control Protocol (TCP) which is one of the famous protocols in TCP/IP stack and in IoT.
What is TCP?
The Transmission Control Protocol, or TCP protocol for short, is a standard for exchanging data between different devices in a computer network. This protocol dates back to 1973, when computer scientists Robert E. Kahn and Vinton G. Cerf published the first version of the standard as part of a research paper. However, it took another eight years before TCP was standardized in RFC 793. Since then, there have been a number of improvements and extensions, although the core of the protocol has remained unchanged.
The current version, which is defined in RFC 7323 is from 2014. The current version of the TCP protocol allows two endpoints in a shared computer network to establish a connection that enables a two-way transmission of data. Any data loss is detected and automatically corrected, which is why TCP is also called a reliable protocol. The term TCP/IP protocol stack is also commonly used to refer to the Internet protocol suite since the TCP protocol is almost always based on the Internet protocol (IP) and this connection is the foundation for the majority of public and local networks and network services.
TCP allows for transmission of information in both directions. The protocol uses segments (packets) as the basic units of data transmission. In addition to the payload, segments can also contain control information and are limited to 1,500 bytes. The TCP software in the network protocol stack of the operating system is responsible for establishing and terminating the end-to-end connections as well as transferring data.
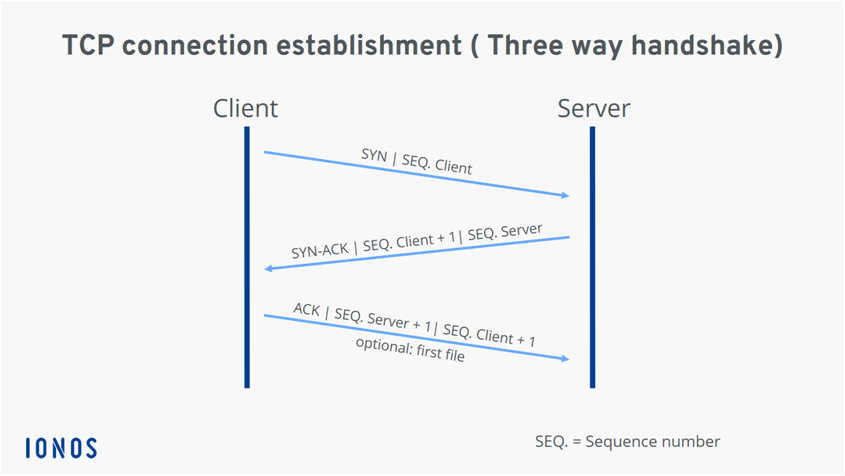
The TCP software is controlled by the various network applications, such as web browsers or servers, via specific interfaces. Each connection must always be identified by two clearly defined endpoints (client and server). It doesn’t matter which side assumes the client role and which assumes the server role. All that matters is that the TCP software is provided with a unique, ordered pair consisting of IP address and port (also referred to as “2-tuple” or “socket”) for each endpoint. TCP 3-way handshake for connection establishment is as shown below.
Prerequisites for establishing a valid TCP connection: Both endpoints must already have a unique IP address (IPv4 or IPv6) and have assigned and enabled the desired port for data transfer. The IP address serves as an identifier, whereas the port allows the operating system to assign connections to the specific client and server applications. First, the requesting client sends the server a SYN packet or segment (SYN stands for synchronize) with a unique, random number.
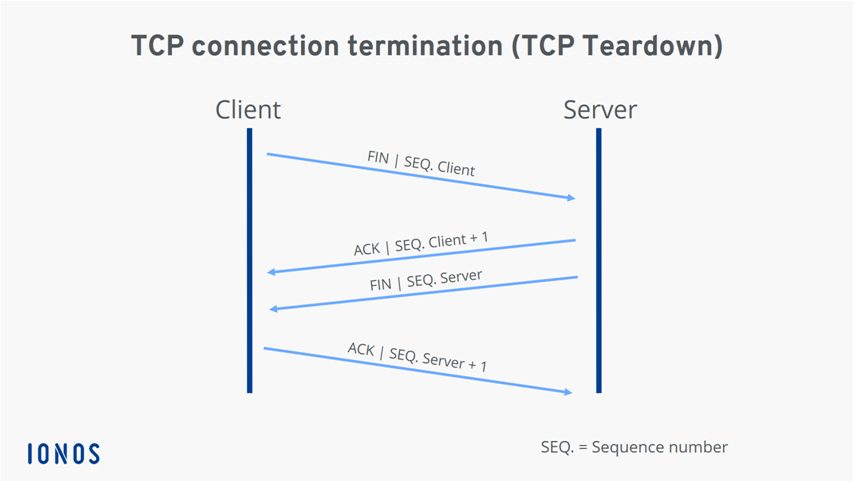
If the server has received the segment, it agrees to the connection by returning a SYN-ACK packet (ACK stands for acknowledgment) including the client’s sequence number plus 1. It also transmits its own sequence number to the client. Finally, the client acknowledges the receipt of the SYN-ACK segment by sending its own ACK packet, which in this case contains the server’s sequence number plus 1. At the same time, the client can already begin transferring data to the server. Since the TCP connection is established in three steps, the connection process is called a three-way handshake. TCP connection teardown is illustrated in the figure below.
TCP Header
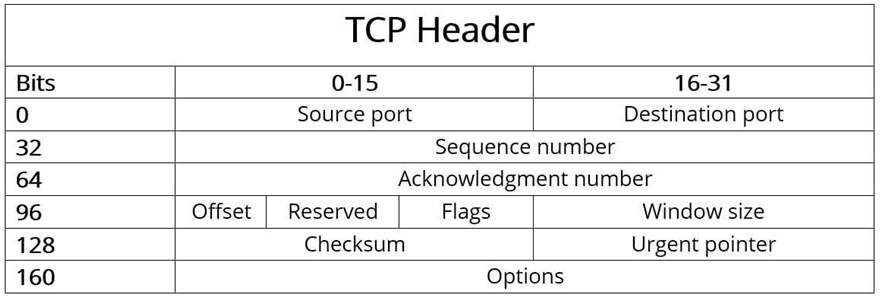
Typically, the header of a TCP packet contains the data required for connection and data transmission with the Transmission Control Protocol. This header data (which contains control information) precedes the payload to be transferred and is typically 20 bytes (160 bits) in size. It is followed by up to 40 bytes (320 bits) of additional information, which is optional and not used in all packets. TCP segments without payload data, essentially pure headers, are also allowed if only acknowledgments, error messages, etc. need to be transmitted, as in the case of SYN and FIN messages (connection establishment/termination). TCP header is shown below.
Source port (16 bits): Identifies the port number of the sender.
Destination port (16 bits): Identifies the port number of receiver.
Sequence number (32 bits): The sequence number specifies the first byte of attached payload data or is sent when the connection is established or terminated. It is also used for validating and sorting the segments after transmission.
Acknowledgment number (32 bits): This field contains the next sequence number that the sender is expecting. An ACK flag (in the “Flags” field) is a precondition for validity.
Offset (4 bits): The “Offset” field specifies the length of the TCP header in 32-bit words to highlight the starting point of the payload data. This starting point varies from segment to segment due to the variable “Options” field.
Reserved (6 bits): Reserved for future use according to RFC 793 and not yet in use. This field must always be set to 0.
Flags (6 bits): The six possible single bits in the “Flags” field enable various TCP actions for organizing communication and data processing. The following flags are either set or not set for these actions:
- URG: The “Urgent” flag signals to the TCP application that the payload data must be processed immediately up to the set Urgent pointer (see above).
- ACK: In combination with the acknowledgment number, the ACK flag acknowledges the receipt of TCP packets. If the flag is not set, the confirmation number is also invalid.
- PSH: The “Push” flag ensures that a TCP segment is immediately pushed through without first being sent to the buffer of the sender and receiver.
- RST: If there is an error during transmission, a TCP packet with the RST flag set can be used to reset the connection.
- SYN: Messages that have SYN flag set represent the first step of the three-way handshake, meaning they initiate the connection.
- FIN: The “Finish” flag signals to the other party that a sender is ending the transmission.
Window size (16 bits): This field specifies the number of bytes that the sender is willing to receive.
Checksum (16 bits): The Transmission Control Protocol can reliably detect transmission errors. The checksum calculated from the header, the payload data and the pseudo-header is used for this purpose.
Urgent pointer (16 bits): The urgent pointer indicates the position of the first byte after the payload data that is to be processed urgently. As a result, this field is only valid and relevant if the URG flag is set.
Options (0 – 320 bits): Use the Options field if you want to include TCP functions that don’t belong in the general header, for example if you want to define the maximum segment size. The length of the options must always be a multiple of 32, otherwise zero-bit padding is required.

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.



Leave a Reply