In this article we will look at different IoT enabling technologies like wireless sensor networks, cloud computing, etc.
Different technologies together enable development of IoT applications. The IoT enabling technologies are:
- Wireless Sensor Networks
- Cloud Computing
- BigData Analytics
- Communication Protocols
- Embedded Systems
Watch this video to learn about IoT enabling technologies:
Contents
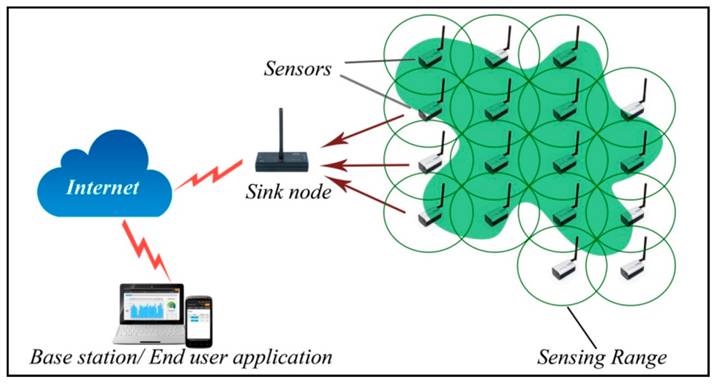
IoT Enabling Technologies: Wireless Sensor Networks
A Wireless Sensor Network (WSN) is a collection of devices which communicate through wireless channels. A WSN consists of distributed devices with sensors which are used to monitor the environmental and physical conditions.
A WSN consists of a number of end nodes, routers and coordinators. End nodes can also act as routers. A coordinator collects data from all the nodes and is connected to Internet.
Examples of WSNs used in IoT systems:
- Weather monitoring systems
- Indoor air quality monitoring systems
- Soil moisture monitoring systems
- Surveillance systems
- Smart grids
- Structural health monitoring systems
IoT Enabling Technologies: Cloud Computing
Cloud computing is a computing model in which applications and services are delivered over Internet. The resources provisioned by cloud can be compute, networking or storage. Cloud allows the users to access resources based on utility model. The characteristics of cloud computing are:
- On demand: The resources in the cloud are available based on the traffic. If the incoming traffic increases, the cloud resources scale up accordingly and when the traffic decreases, the cloud resources scale down accordingly.
- Autonomic: The resource provisioning in the cloud happens with very less to no human intervention. The resources scale up and scale down automatically.
- Scalable: The cloud resources scale up and scale down based on the demand or traffic. This property of cloud is also known as elasticity.
- Pay-per-use: On contrary to traditional billing, the cloud resources are billed on pay-per-use basis. You have to pay only for the resources and time for which you are using those resources.
- Ubiquitous: You can access the cloud resources from anywhere in the world from any device. All that is needed is Internet. Using Internet you can access your files, databases and other resources in the cloud from anywhere.
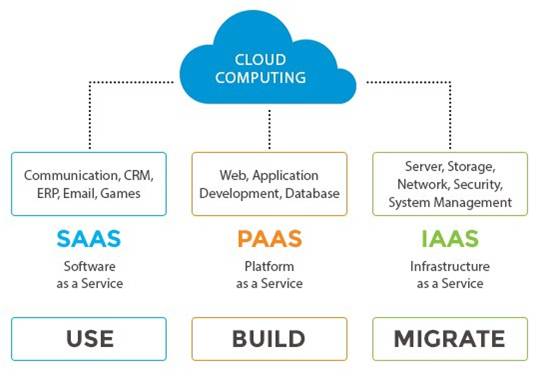
Cloud computing offers three basic service models using which users can subscribe to cloud resources. These service models are:
- Infrastructure-As-A-Service (IAAS)
- Platform-As-A-Service (PAAS)
- Software-As-A-Service (SAAS)
These three service models can be illustrated as shown below. IAAS model provides the core infrastructure to companies for building their own applications. This core infrastructure includes servers, storage, networking, etc. PAAS model offers development runtimes for the users to build and deploy their application. SAAS model offers already developed and deployed applications for the users to use. Examples of SAAS offerings are Gmail, Facebook, DropBox, YouTube, etc.
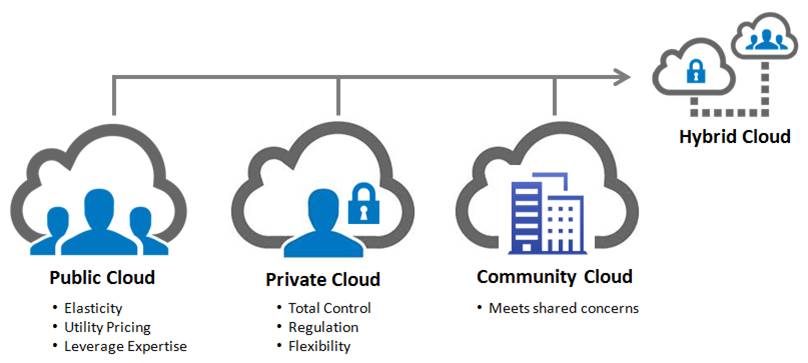
Cloud computing supports four basic deployment models. These models differ in the way how the cloud is built and who are using the resources in the cloud. The four cloud deployment models are:
- Public cloud
- Private cloud
- Community cloud
- Hybrid cloud
In a public cloud the resources are shared between several users. Public cloud is generally maintained by the cloud service provider. The management of the resources is taken care by the cloud service provider. In a private cloud all the resources are used by a single organization. Such organization has the complete control on the cloud and can follow all the necessary regulations. Private cloud offeres greater flexibility when compared to the public cloud.
A community cloud is one whose resources are shared by two or more companies having shared goals. Such clouds are generally used for conducting collaborated research. A combination of the previous three clouds is a hybrid cloud. Big companies generally use hybrid cloud. The companies generally store the sensitive data in the private cloud and other non-sensitive data in the public cloud. These four types of cloud deployments are summarized in the below figure.
IoT Enabling Technologies: BigData Analytics
BigData is a collection of data coming from various types of sources. The data is often huge which cannot be handled by the traditional databases and data warehouses. BigData is often characterized by six Vs. They are:
- Volume: Refers to the huge volume of data aggregated from various sources.
- Variety: Refers to different types of data. Data can be structured, semi-structured or unstructured.
- Velocity: Refers to the speed at which the data is generated. Now-a-days the amount of data available on the Internet per minute is several peta bytes or even more.
- Veracity: Refers to the degree to which the data can be trusted. If the data collected is incorrect or has manipulated or wrong values, the analysis of such data is useless.
- Value: Refers to the business value of the collected. Even though we have huge amount of data, but it is not useful for gaining profits in the business, such data is useless.
- Variability: Refers to the ways in which the big data can be used and formatted.
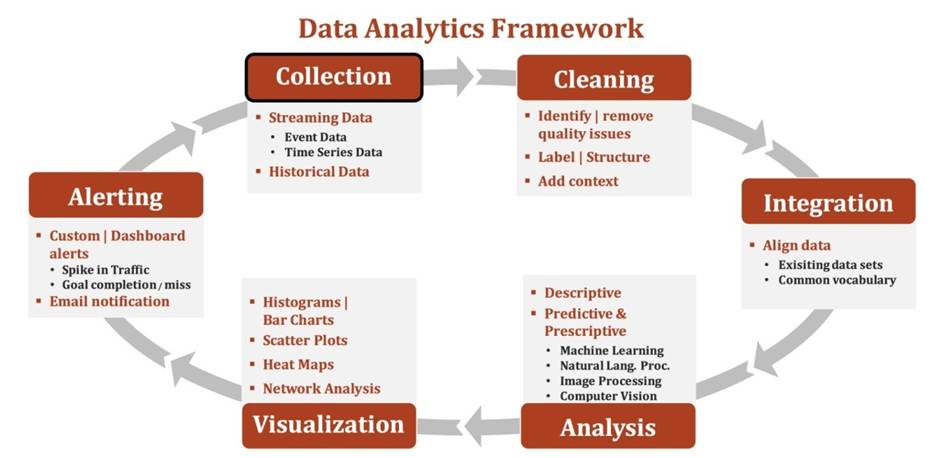
The data analytics framework consists of six steps namely: collection, cleaning, integration, analysis, visualization and alerting. These six steps can be summarized as shown in the below figure.
IoT Enabling Technologies: Communication Protocols
Communications protocols form the backbone for IoT systems. They allow devices to communicate with each other. Protocols define the data exchange formats, data encoding and addressing schemes for devices. Protocols also provide flow control, error control, and other functions.
IoT Enabling Technologies: Embedded Systems
Embedded system can be imagined as computing hardware with software embedded in it. An embedded system can be an independent system or it can be a part of another larger system.
An embedded system is a microcontroller or microprocessor based system which is designed to perform a specific task. The key components include microcontroller/micrprocessor, memory, networking units, I/O, and storage. It runs Real-Time Operating Systems (RTOS).
An embedded system has three components. They are:
- Hardware
- Software
- Real Time Operating system (RTOS) that supervises the application software and provide mechanism to let the processor run a process as per schedule by following a plan to control the latencies
The characteristics of an embedded system are:
- Single-functioned
- Tightly constrained
- Reactive and Real time
- Memory
- Connected

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.



Leave a Reply