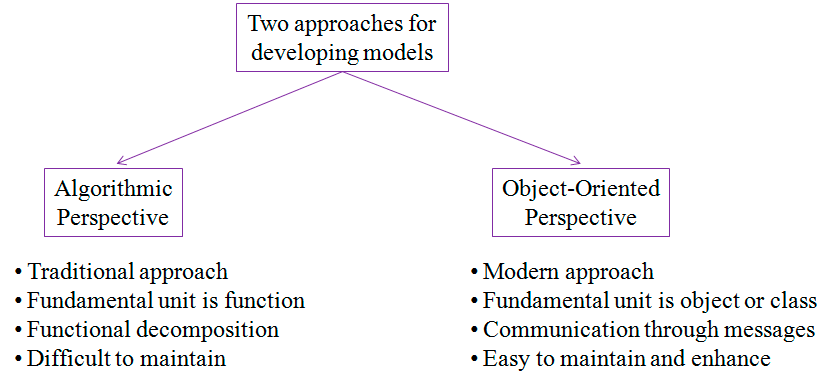
In software field, there are several ways to approach for building a model. The two most common ways are: from an algorithmic perspective and from an object oriented perspective.
The traditional view of software development takes an algorithmic perspective. In this approach, the main building block of all software is the procedure or function. This view leads the developers to focus on issues of control and the decomposition of larger algorithms into smaller ones.
As requirements change, and the system grows, systems built with an algorithmic focus turn out to be very hard to maintain.
The contemporary (another) view of software development takes an object oriented perspective. In object oriented modeling, the main building block of all software systems is the object or class.
Simply put, an object is a thing, generally drawn from the elements of the problem space or the solution space. A class is a description of a set of common objects. Every object has state, identity and behavior.
For example, consider simple three-tier architecture for a billing system, involving a user interface, middleware, and a database. In the user interface, you will find concrete objects such as buttons, menus and dialog boxes.
In the database you will find concrete objects such as tables representing entities from the problem domain, including customers, products and orders. In the middle layer, you will find objects such as transactions and business rules.
The object oriented approach to software development is a part of the mainstream development simply because it has proven to be of value in building systems in all sorts of problem domains and cover all degrees of size and complexity.

Suryateja Pericherla, at present is a Research Scholar (full-time Ph.D.) in the Dept. of Computer Science & Systems Engineering at Andhra University, Visakhapatnam. Previously worked as an Associate Professor in the Dept. of CSE at Vishnu Institute of Technology, India.
He has 11+ years of teaching experience and is an individual researcher whose research interests are Cloud Computing, Internet of Things, Computer Security, Network Security and Blockchain.
He is a member of professional societies like IEEE, ACM, CSI and ISCA. He published several research papers which are indexed by SCIE, WoS, Scopus, Springer and others.
Leave a Reply